Working for Jisc means that I’m increasingly on-the-road, which inevitably makes me a user of more and more Wi-Fi Hotspots; whether they be at the offices, campus or buildings of our Jisc members, at hotels, cafes, or on public transport.
I continue to be surprised at the compromises that are being made to deliver Wi-Fi, either compromising security, because my data is then unencrypted (at Layer 1 of the OSI model at least), or to accountability/traceability, so the operator of the Wi-Fi has left little recourse in the event that I am a malicious user.
Examples of bad Wi-Fi
Here are a few examples, I’ve gathered on my travels:
- Hotel with either an ‘open network’ with no further authentication or authorisation process
- The kicker with this one is that they are a hotel chain and I’ve stayed in a number of their hotels, which all suffer the same issue
- Hotel with a (now probably widely circulated) ‘secured network’ with WEP key
- An independent hotel, but in an extremely busy and central location
- Wired Equivalent Privacy (WEP), is widely-known as a weak security standard. It was deprecated in 2004, and from 2005 there were known vulnerability instances in the public domain (for example the Café Latte attack)
- Conference venue with a ‘secured network’ with WPA2 key for their wireless network but easily guessable and potential to be widely shared
- Educational organisation ‘Secured network’ with WPA2 key for their wireless network but easily guessable and potential to be widely shared
- This organisation should be fully utilising Jisc’s eduroam service
- Educational organisation ‘open network’ with further authentication or authorisation process utilising a widely shared username and password
- Again, this organisation should be fully utilising Jisc’s eduroam service
Home Wi-Fi in the workplace

What we see is that increasingly organisations have deployed a solution suitable for the home e.g. a shared key using the WPA2-PSK security method. At home your accountability risk should be low, you may have shared your key with a few friends and family, but there is a level of trust that will not be there in a public or commercial setting. Increasingly home users don’t carry their key over when they change ISP or broadband router and simply reconfigure their devices, this serves to routinely clear out older users.
Guest Wi-Fi
For Jisc members who are connected to the Janet network, is that any Wi-Fi solution should comply with our Guest and Public network access policy, and that many of the poor solutions mentioned are unlikely to comply with the policy. Jisc offer a Public access to the internet via the Janet network service, which is currently provided by ‘The Cloud’.
eduroam
No surprise that I’m a big advocate for eduroam and its increasing footprint, which aside from being an excellent solution for roaming, also deals with security and accountability well, so should be used as the de-facto solution for users in education (especially Jisc members as we are the UK provider of eduroam).
eduroam is an implementation of 802.1x/WPA2 AES, so the trade-off is that to setup an initial connection with all the correct security controls can be more challenging than a network using Pre-Shared key (PSK) or captive portal. However, we have tools such as eduroam CAT to help organisations and users with this challenge, and we absolutely need to getting organisations and their users to use these tools (we call this process of using tools to configure the WiFi network on-boarding).
It should be no surprise, but if you by-pass security controls, then bad things happen, so a poorly configured 802.1x device can be susceptible to a Man-in-the Middle (MITM) attack (See this blog post on hostapd-wpe which can be used to achieve this).
Man-in-the-middle attacks
Man-in-the-Middle attacks are highly possible on Wi-Fi networks, the first step is defeating Layer 1 of the OSI model; so on an open network or Pre-shared key based on WEP, won’t require a lot of skill, and thus as organisations we should avoid using these as much as possible.
Pre-shared keys based on WPA2-PSK in small deployments like your Home are brilliant, but their security will decline as the user numbers increase, and the trust between the users diminishes, because anyone who knows the key can decrypt any data on that network.
802.1x/WPA2 AES the basis of eduroam is better because encryption is between each device and the access point, and is not shared.
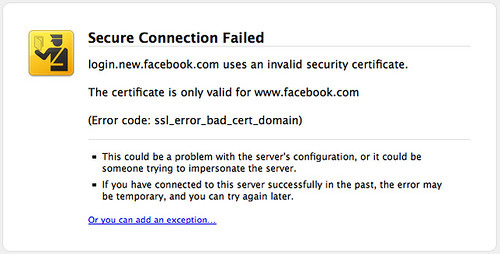
Once the above is decrypted then you are at the point of tricking users or their devices, which is usually at Layer 2 and above in the OSI model. ARP spoofing, rogue DHCP servers, intercepting proxies which issue SSL/TLS Certificate errors, with the hope that users tell their device to send data to the untrusted client (and many of them will because how many IT people have told them to ‘by-pass the security controls’ in the past?).
Devices like the WiFi pineapple make it much easier to setup this type of rogue network. There is of course with every ‘hackers tool’ a valid reason to have and use a WiFi pineapple as the operator of a WiFi network.
What are the risks to the organisation?
In terms of Information Security and thinking about the ISO 27001 standard, which some organisations are trying to achieve by ensuring the Confidentiality, Integrity and Availability of information and services. These could be compromised via the Wi-Fi network, and so it’s likely to figure as an issue against a number of the controls that form part of the ISMS (Information Security Management System), which is developed as part of ISO 27001.
If you don’t have robust authentication and authorisation, then you could easily become a source of a Distributed Denial of Service attacks, Copyright Infringement, other unlawful or potential risky activity. If you are known to have a widely open and unaccountable network, then this information may circulate from your organisation users to people who aren’t.
One potential area of risky activity to consider is what happened if you became an exit point from the ‘Dark Web’ to the Internet (called a ToR exit node), and you also had no accountability for any usage of the Wi-Fi? There are lots of example of individuals who have run Tor exit node and whose IT equipment has been seized by authorities in the event of illegal activity. Imagine if these data and servers were your organisation’s key infrastructure?
There is a risk of gain unauthorised access to internal Local Area Network (LAN) via the Wi-Fi, which could result in an information security breach or hacking attempt on corporate systems such as those holding financial or personal data. I increasingly find that small organisations have no separation between Public Wi-Fi and their corporate LAN, a simple arp-scan, or port scan would often confirm that situation in moments, if the internal network is the same logical network (shared VLAN) then you are also potentially exposing the LAN to the MITM attack.
What can organisations do?
At your organisation locations, ensure you have a robust WiFi access solution, and treat it a priority area. Bring your own device isn’t going away, and increasingly people turn up to a location and want WiFi access.
For Jisc members I would recommend a combination of eduroam (with correct on-boarding instructions or tools for users), and exploring our Public access service provided via The Cloud.
You shouldn’t need a lot else, eduroam can deal with most organisation requirements, with a Public access service to cover the general public and visitors who aren’t participating in eduroam.
For non-Jisc members you could explore 802.1x/WPA2 Enterprise (the technology we used behind eduroam), but you may need to prepare for additional costs in terms of on-boarding that this may entail.
Some things to definitely do:
- Avoid running unsecure Wi-Fi networks and those using older protocols (WPA, TKIP, WEP etc.)
- Key-based networks should only be used for small groups of users, if used larger then keys should be changed very regularly
- Do not run hidden networks, these may be more susceptible to the device being hi-jacked as rather than the network (SSID) being advertised your device is constantly announcing that it wants to connect to that network (and your attacker with the Wi-Fi pineapple will go ‘sure it’s over here’?)
- Implement access controls between on the network, particularly those used for Guest and BYOD and other networks i.e. using a Firewall
Discuss with your Jisc account manager and gain access to Subject specialists in organisational infrastructure, as well as the technical experts from Jisc’s eduroam UK support team.
What can users do?
There is a very interesting blog post here on How Safe is Public Wi-Fi, on this topic. I would suggest the following:
- If you have access to eduroam then configure it (if you’ve not configured eduroam via a tool such as eduroam CAT, or manually configured certificate information, then this may not be correct, contact your organisation IT service for support)
- If you have access to other 802.1x WPA2 Enterprise (AES) networks use those (noting again the above about configuration)
- Regularly ‘forget’ any open SSIDs on your devices that you no longer need
- Invest in or provide yourself a VPN service, which ensures you have some encryption. See this article from BBC News on using a RaspberryPI to create a VPN
- Ensure you use secure protocols in your application, so HTTPS rather than HTTP, IMAPS rather than IMAP etc.
- Do not by-pass security controls either in configuring your device or in later use, for instance if you get an SSL/TLS Certificate warning, treat with caution
The future
I hope the future is increased take-up of Wi-Fi Certified Passpoint (formerly Hotspot 2.0), which builds on and uses some of the technology in 802.1x/WPA2 Enterprise, but there is a lot of Wi-Fi equipment out there, both at the consumer and organisation end. So it’s going to take time to trickle through…
